內容目錄
麼是Envoy Gateway?
Envoy Gateway 是一個用於管理Envoy Proxy 的開源項目,可單獨使用或作為Kubernetes 中應用的網關。它通過了Gateway API 核心一致性測試,使用Gateway API 作為其唯一的配置語言來管理Envoy 代理,支持GatewayClass、Gateway、HTTPRoute和 TLSRoute 資源。
Envoy Gateway 的目標是降低用戶採用Envoy 作為API 網關的障礙,以吸引更多用戶採用Envoy。它通過入口和L4/L7 流量路由,表達式、可擴展、面向角色的API 設計,使其成為供應商建立API 網關增值產品的基礎。
Envoy Gateway 的核心優勢是輕量級、開放、可動態編程,尤其是為後端增加了安全功能,這些優勢使得它很適合作為後端API 網關。
架構
下圖展示的是Envoy Gateway 的架構,圖中的陰影部分錶示是Envoy Gateway。你可以通過靜態和動態兩種方式來配置它,其中的Provider 是針對不同的供應商開發的。
安裝Envoy Gateway
[root@dev-rancher EnvoyGateway]# kubectl apply -f https://github.com/envoyproxy/gateway/releases/download/v0.2.0/install.yaml namespace/envoy-gateway-system created namespace/gateway-system created customresourcedefinition.apiextensions.k8s.io/envoyproxies.config.gateway.envoyproxy.io created customresourcedefinition.apiextensions.k8s.io/gatewayclasses.gateway.networking.k8s.io configured customresourcedefinition.apiextensions.k8s.io/gateways.gateway.networking.k8s.io configured customresourcedefinition.apiextensions.k8s.io/httproutes.gateway.networking.k8s.io configured customresourcedefinition.apiextensions.k8s.io/referencegrants.gateway.networking.k8s.io created customresourcedefinition.apiextensions.k8s.io/referencepolicies.gateway.networking.k8s.io created customresourcedefinition.apiextensions.k8s.io/tcproutes.gateway.networking.k8s.io created customresourcedefinition.apiextensions.k8s.io/tlsroutes.gateway.networking.k8s.io created customresourcedefinition.apiextensions.k8s.io/udproutes.gateway.networking.k8s.io created serviceaccount/certgen created serviceaccount/envoy-gateway created serviceaccount/gateway-api-admission created role.rbac.authorization.k8s.io/certgen created role.rbac.authorization.k8s.io/infra-manager created role.rbac.authorization.k8s.io/leader-election-role created role.rbac.authorization.k8s.io/gateway-api-admission created clusterrole.rbac.authorization.k8s.io/envoy-gateway-role created clusterrole.rbac.authorization.k8s.io/gateway-api-admission created clusterrole.rbac.authorization.k8s.io/metrics-reader created clusterrole.rbac.authorization.k8s.io/proxy-role created rolebinding.rbac.authorization.k8s.io/certgen created rolebinding.rbac.authorization.k8s.io/infra-manager created rolebinding.rbac.authorization.k8s.io/leader-election-rolebinding created rolebinding.rbac.authorization.k8s.io/gateway-api-admission created clusterrolebinding.rbac.authorization.k8s.io/gateway-api-admission created clusterrolebinding.rbac.authorization.k8s.io/envoy-gateway-rolebinding created clusterrolebinding.rbac.authorization.k8s.io/proxy-rolebinding created configmap/envoy-gateway-config created service/envoy-gateway created service/envoy-gateway-metrics-service created service/gateway-api-admission-server created deployment.apps/envoy-gateway created deployment.apps/gateway-api-admission-server created job.batch/certgen created job.batch/gateway-api-admission created job.batch/gateway-api-admission-patch created validatingwebhookconfiguration.admissionregistration.k8s.io/gateway-api-admission created
[root@dev-rancher EnvoyGateway]# kubectl get pods --namespace gateway-system NAME READY STATUS RESTARTS AGE gateway-api-admission-bvptn 0/1 Completed 0 7s gateway-api-admission-patch-l967z 0/1 Completed 0 6s gateway-api-admission-server-5bf65c669b-67sjq 0/1 ContainerCreating 0 8s
[root@dev-rancher EnvoyGateway]# kubectl api-resources | grep gateway.networking gatewayclasses gc gateway.networking.k8s.io/v1beta1 false GatewayClass gateways gtw gateway.networking.k8s.io/v1beta1 true Gateway httproutes gateway.networking.k8s.io/v1beta1 true HTTPRoute referencegrants refgrant gateway.networking.k8s.io/v1alpha2 true ReferenceGrant referencepolicies refpol gateway.networking.k8s.io/v1alpha2 true ReferencePolicy tcproutes gateway.networking.k8s.io/v1alpha2 true TCPRoute tlsroutes gateway.networking.k8s.io/v1alpha2 true TLSRoute udproutes gateway.networking.k8s.io/v1alpha2 true UDPRoute
[root@dev-rancher EnvoyGateway]# kubectl get pods --namespace envoy-gateway-system NAME READY STATUS RESTARTS AGE envoy-gateway-6bd456488c-jf8zx 2/2 Running 0 3m
安裝測試應用
[root@dev-rancher EnvoyGateway]# kubectl apply -f https://raw.githubusercontent.com/istio/istio/master/samples/httpbin/httpbin.yaml serviceaccount/httpbin created service/httpbin created deployment.apps/httpbin created
[root@dev-rancher EnvoyGateway]# kubectl get pods -n default | grep httpbin httpbin-847f64cc8d-mxl6v 1/1 Running 0 26m
配置Envoy Gateway
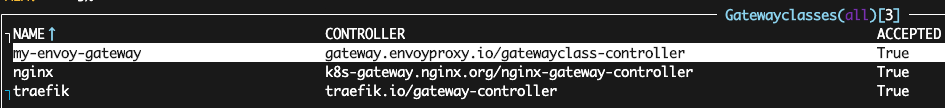
$ kubectl apply -f - <<EOF apiVersion: gateway.networking.k8s.io/v1beta1 kind: GatewayClass metadata: name: my-envoy-gateway spec: controllerName: gateway.envoyproxy.io/gatewayclass-controller EOF
我們可以看到關於這個新實例的一些有限信息,假設我們的描述是有效的,我們將看到ACCEPTED: True。
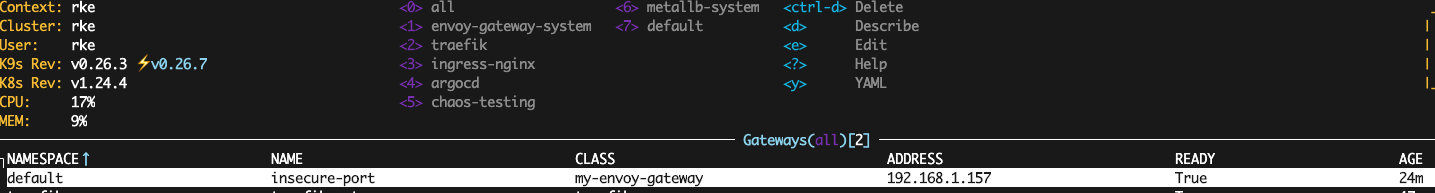
$ kubectl apply -f - <<EOF
apiVersion: gateway.networking.k8s.io/v1beta1
kind: Gateway
metadata:
name: insecure-port
spec:
gatewayClassName: my-envoy-gateway
listeners:
- name: http
protocol: HTTP
port: 8080
EOF
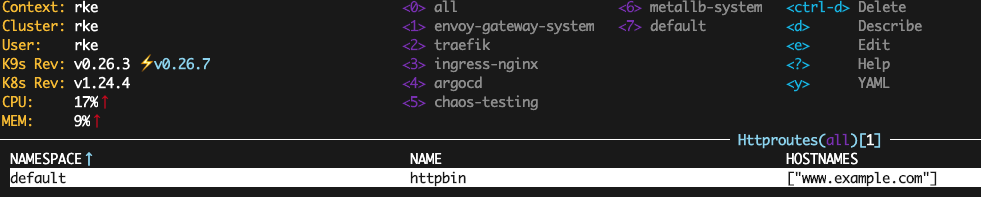
$ kubectl apply -f - <<EOF
apiVersion: gateway.networking.k8s.io/v1beta1
kind: HTTPRoute
metadata:
name: httpbin
spec:
parentRefs: [ {name: insecure-port} ]
hostnames: ["www.example.com"]
rules:
- matches:
- path: {type: PathPrefix, value: /}
backendRefs:
- {group: "", kind: Service, name: httpbin, port: 8000, weight: 1}
EOF
檢查這種資源目前並沒有向我們展示太多東西,但我們可以看到它至少已部署成功。
[root@dev-rancher EnvoyGateway]# kubectl get pods -n envoy-gateway-system NAME READY STATUS RESTARTS AGE envoy-default-insecure-port-64656661-5dbf74d87-gqts9 1/1 Running 0 5m47s envoy-gateway-6bd456488c-jf8zx 2/2 Running 0 16
測試流量
[root@dev-rancher EnvoyGateway]# kubectl get svc -n envoy-gateway-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE envoy-default-insecure-port-64656661 LoadBalancer 10.43.190.253 192.168.1.157 8080:30978/TCP 26m envoy-gateway ClusterIP 10.43.192.54 <none> 18000/TCP 36m envoy-gateway-metrics-service ClusterIP 10.43.155.250 <none> 8443/TCP 36m
curl --header "Host: www.example.com" 192.168.1.157:8080/headers
回應如下
{
"headers": {
"Accept": "*/*",
"Host": "www.example.com",
"User-Agent": "curl/7.29.0",
"X-Envoy-Expected-Rq-Timeout-Ms": "15000"
}
}