官網 https://docs.traefik.io/
Traefik簡介
ingress相當於從kubernetes複製到外部訪問可訪問的入口,將用戶的URL請求轉發到不同的服務上。Ingress相當於nginx,apache等負載均衡反向代理服務器,其中還包括規則定義,即URL的路由信息。
Traefik是一種開源的反向的代理與負載均衡工具。它最大的優點是能夠與常見的微服務系統直接整合,實現自動化動態配置。Trafik通過不斷地跟kubernetes API打交道,實時的感知定位服務, pod等變化,例如pod,服務增加與減少等;當得到這些變化信息後,Ingress自動更新配置並熱重載,達到服務發現的作用。
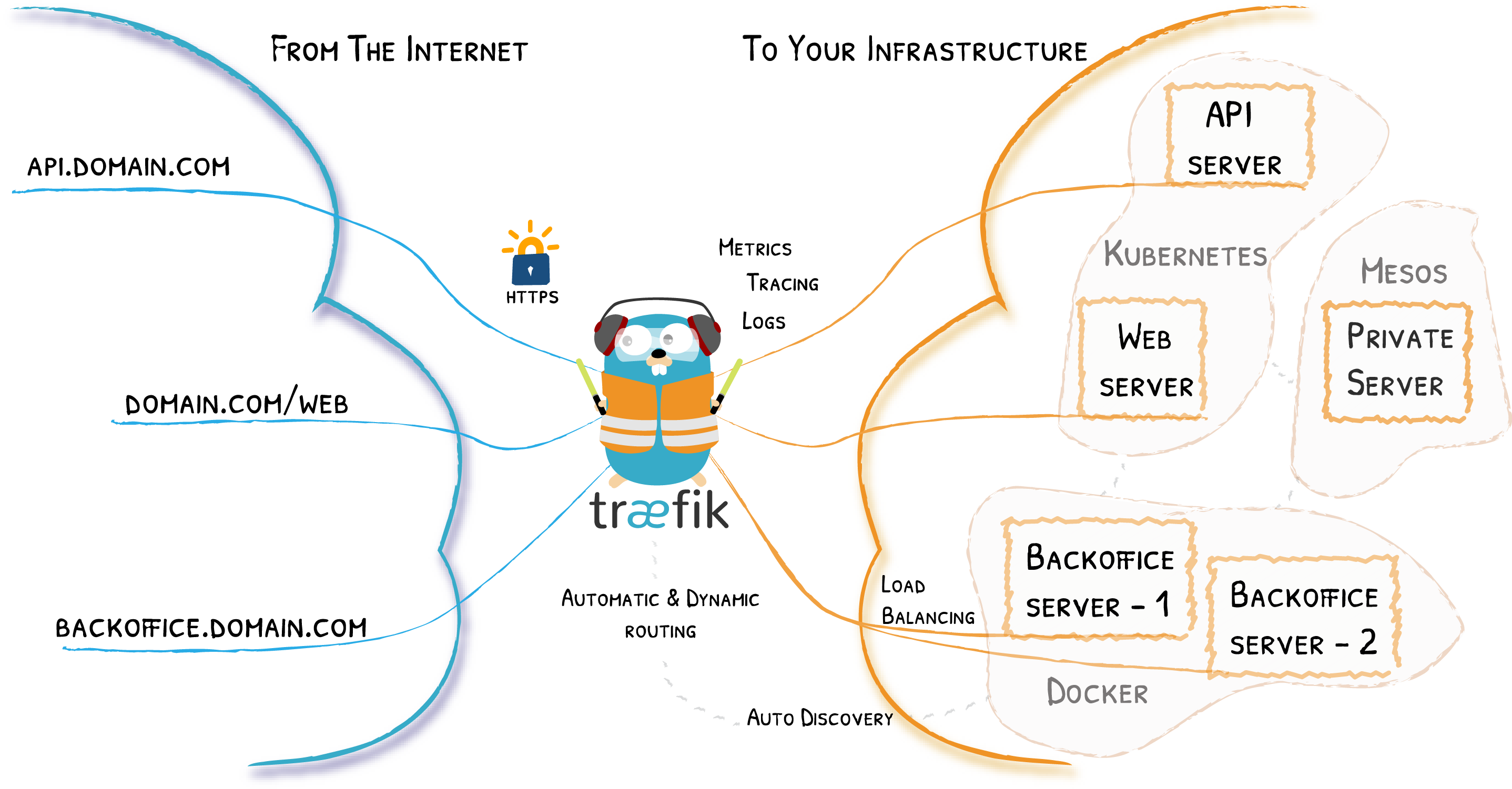
traefik整體架構如下所示。
建置環境minikube
mkdir traefik
vi traefik-system.yaml
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: ingressroutes.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: IngressRoute
plural: ingressroutes
singular: ingressroute
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: middlewares.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: Middleware
plural: middlewares
singular: middleware
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: tlsoptions.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: TLSOption
plural: tlsoptions
singular: tlsoption
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: ingressroutetcps.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: IngressRouteTCP
plural: ingressroutetcps
singular: ingressroutetcp
scope: Namespaced
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: traefik
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- "extensions"
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- "traefik.containo.us"
resources:
- middlewares
- ingressroutes
- ingressroutetcps
- tlsoptions
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: traefik
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik
subjects:
- kind: ServiceAccount
name: traefik
namespace: traefik-system
---
apiVersion: v1
kind: Namespace
metadata:
name: traefik-system
---
apiVersion: v1
data:
config.yaml: |
serversTransport:
insecureSkipVerify: true
api:
insecure: true
dashboard: true
debug: true
metrics:
prometheus: ""
entryPoints:
web:
address: ":80"
forwardedHeaders:
insecure: true
websecure:
address: ":443"
forwardedHeaders:
insecure: true
providers:
kubernetesCRD: ""
log:
filePath: ""
level: error
format: json
accessLog:
filePath: ""
format: json
bufferingSize: 0
filters:
retryAttempts: true
minDuration: 20
fields:
defaultMode: keep
names:
ClientUsername: drop
headers:
defaultMode: keep
names:
User-Agent: redact
Authorization: drop
Content-Type: keep
kind: ConfigMap
metadata:
name: traefik
namespace: traefik-system
---
apiVersion: apps/v1
kind: DaemonSet
#kind: Deployment
metadata:
labels:
app: traefik
name: traefik
namespace: traefik-system
spec:
#replicas: 1
selector:
matchLabels:
app: traefik
template:
metadata:
labels:
app: traefik
spec:
containers:
- args:
- --configFile=/etc/traefik/config.yaml
image: traefik:latest
name: traefik
ports:
- containerPort: 8080
name: admin
protocol: TCP
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
volumeMounts:
- name: config
mountPath: /etc/traefik
volumes:
- name: config
configMap:
name: traefik
serviceAccount: traefik
---
apiVersion: v1
kind: Service
metadata:
name: traefik-ingress
namespace: traefik-system
labels:
app: traefik
spec:
ports:
- name: https
protocol: TCP
port: 443
targetPort: 443
- name: http
protocol: TCP
port: 80
targetPort: 80
type: LoadBalancer
selector:
app: traefik
---
apiVersion: v1
kind: Service
metadata:
name: traefik-admin
namespace: traefik-system
labels:
app: traefik
spec:
ports:
- name: admin
protocol: TCP
port: 8080
targetPort: 8080
type: ClusterIP
selector:
app: traefik
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik
namespace: traefik-system
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: traefik-dashboard
namespace: traefik-system
spec:
entryPoints:
- web
routes:
- match: Host(`traefik-dashboard.itnotetk.com`)
kind: Rule
services:
- name: traefik-admin
port: 8080
middlewares:
- name: ip-ipwhitelist
---
vi traefik-nginx.yaml
---
# declare Traefik deployment
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: nginx-demo
namespace: traefik-system
labels:
app: nginx-demo
spec:
replicas: 1
selector:
matchLabels:
app: nginx-demo
template:
metadata:
labels:
app: nginx-demo
spec:
containers:
- name: nginx
image: "nginx"
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: nginx-http-route
namespace: traefik-system
spec:
entryPoints:
- web
routes:
- match: Host(`nginx.itnotetk.com`)
kind: Rule
services:
- name: nginx-demo
port: 80
middlewares:
- name: redirect
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: nginx-https-route
namespace: traefik-system
spec:
entryPoints:
- websecure
routes:
- match: Host(`nginx.itnotetk.com`)
kind: Rule
services:
- name: nginx-demo
port: 80
- match: Host(`nginx.itnotetk.com`) && Path(`/v2`)
kind: Rule
services:
- name: nginx-demo
port: 80
tls:
secretName: web-ssl
---
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: redirect
namespace: traefik-system
spec:
redirectScheme:
scheme: https
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
protocol: TCP
targetPort: 443
- name: http
tls.key: |
yoursslkey-start...........................................................................................................................yoursslkey-end
---
vi traefik-ipwhitelist.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: ip-ipwhitelist
namespace: traefik-system
spec:
ipWhiteList:
sourceRange:
- 127.0.0.1/32
- 192.168.1.30
kubectl apply -f traefik-system.yaml
kubectl apply -f traefik-nginx.yaml
ubectl apply -f traefik-ipwhitelist.yaml
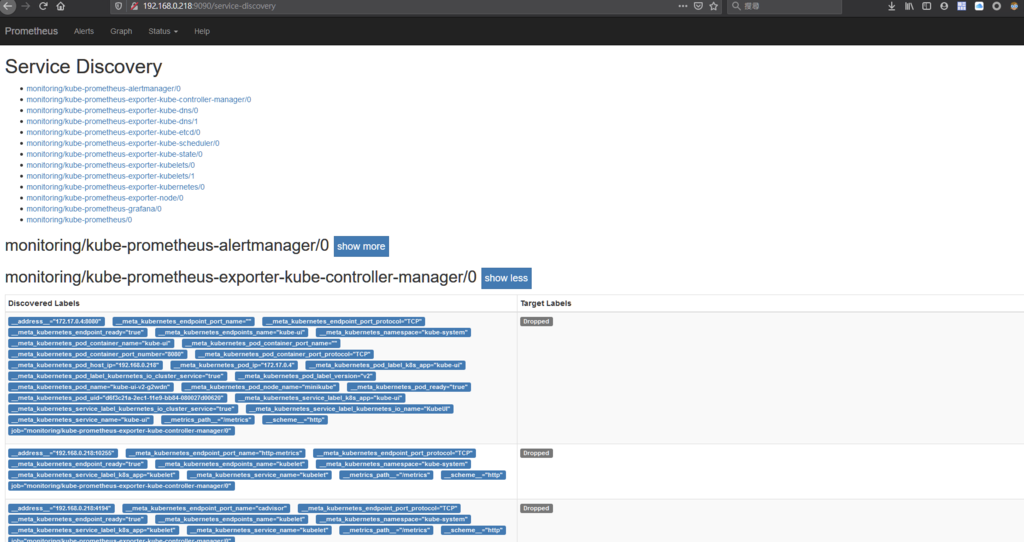
查看資源
kubectl get all -n traefik-system
kubectl -n monitoring get po,svc,cm
kubectl get crd --all-namespaces
kubectl describe secrets/prometheus-kube-prometheus -n monitoring
開啟dashboard監控
kubectl port-forward -n traefik-system svc/traefik-admin --address='0.0.0.0' 8080:8080
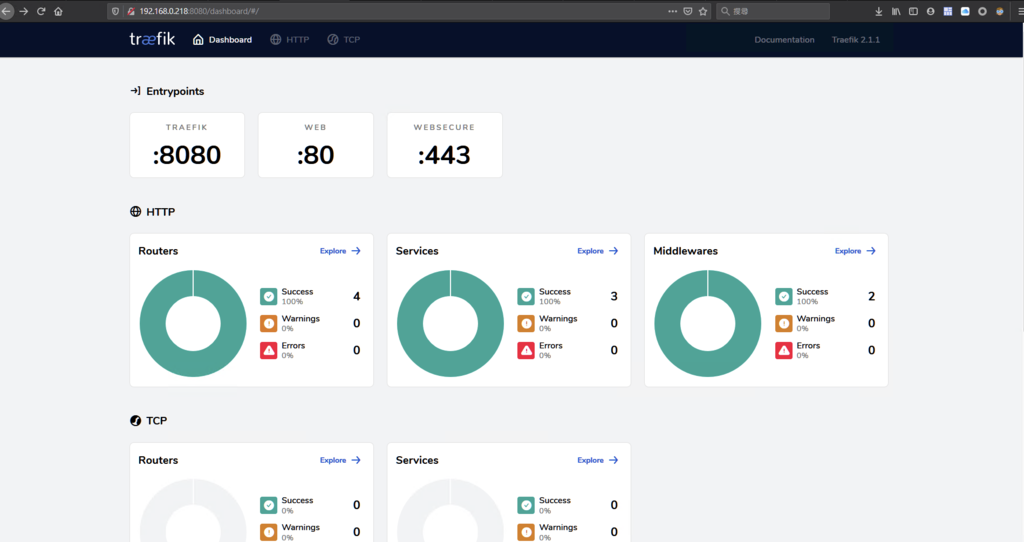
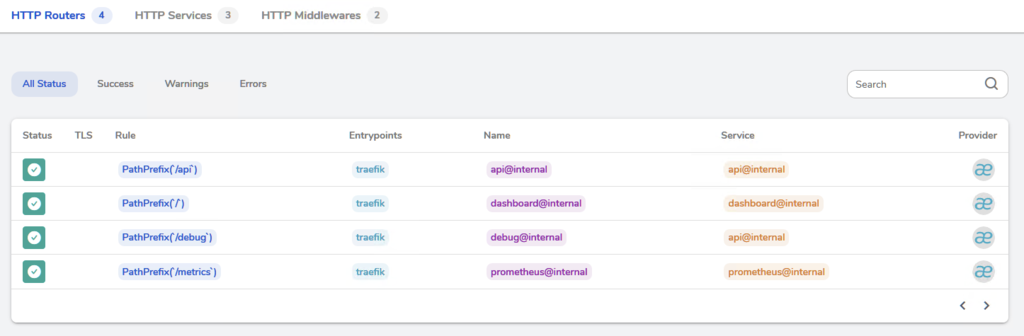
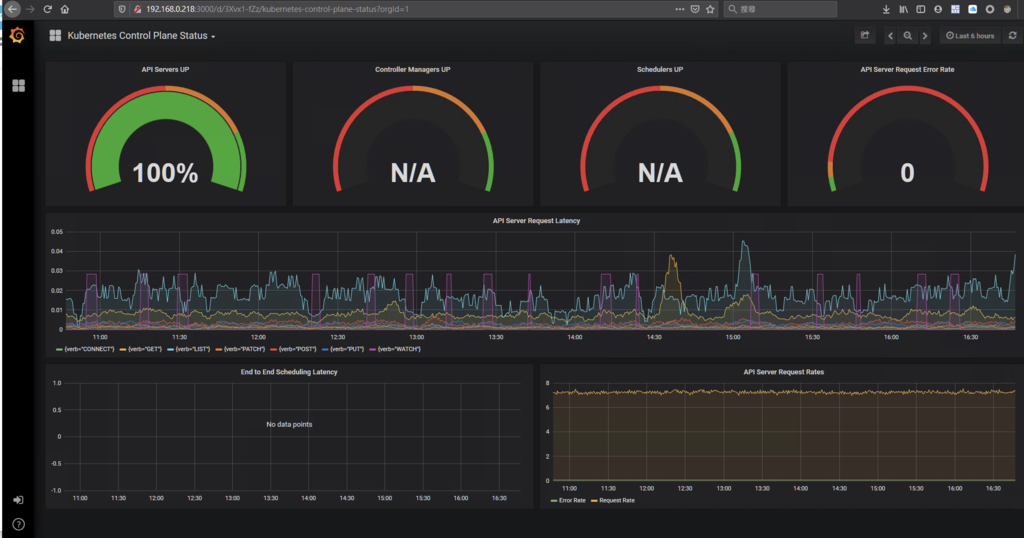
開啟prometheus監控
kubectl port-forward -n monitoring svc/kube-prometheus-grafana --address='0.0.0.0' 3000:80
開啟Prometheus Operator後台
kubectl port-forward -n monitoring service/prometheus-operated --address='0.0.0.0' 9090:9090