腳本來源出處:http://www.vpseek.com/automated-l2tp-over-ipsec-implement-script
Centos安裝腳本
#!/bin/bash
if [ $(id -u) != "0" ]; then
printf "Error: You must be root to run this tool!\n"
exit 1
fi
clear
printf "
####################################################
# #
# This is a Shell-Based tool of l2tp installation #
# Version: 1.2 #
# Author: Zed Lau #
# Website: http://zeddicus.com #
# #
####################################################
"
vpsip=`hostname -i`
iprange="10.0.99"
echo "Please input IP-Range:"
read -p "(Default Range: 10.0.99):" iprange
if [ "$iprange" = "" ]; then
iprange="10.0.99"
fi
mypsk="vpsyou.com"
echo "Please input PSK:"
read -p "(Default PSK: vpsyou.com):" mypsk
if [ "$mypsk" = "" ]; then
mypsk="vpsyou.com"
fi
clear
get_char()
{
SAVEDSTTY=`stty -g`
stty -echo
stty cbreak
dd if=/dev/tty bs=1 count=1 2> /dev/null
stty -raw
stty echo
stty $SAVEDSTTY
}
echo ""
echo "ServerIP:"
echo "$vpsip"
echo ""
echo "Server Local IP:"
echo "$iprange.1"
echo ""
echo "Client Remote IP Range:"
echo "$iprange.2-$iprange.254"
echo ""
echo "PSK:"
echo "$mypsk"
echo ""
echo "Press any key to start..."
char=`get_char`
clear
mknod /dev/random c 1 9
yum -y update
yum -y upgrade
yum install -y ppp iptables make gcc gmp-devel xmlto bison flex xmlto libpcap-devel lsof vim-enhanced
mkdir /ztmp
mkdir /ztmp/l2tp
cd /ztmp/l2tp
wget http://www.openswan.org/download/openswan-2.6.24.tar.gz
tar zxvf openswan-2.6.24.tar.gz
cd openswan-2.6.24
make programs install
rm -rf /etc/ipsec.conf
touch /etc/ipsec.conf
cat >>/etc/ipsec.conf<<EOF
config setup
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
protostack=netkey
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=$vpsip
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
EOF
cat >>/etc/ipsec.secrets<<EOF
$vpsip %any: PSK "$mypsk"
EOF
sed -i 's/net.ipv4.ip_forward = 0/net.ipv4.ip_forward = 1/g' /etc/sysctl.conf
sysctl -p
iptables --table nat --append POSTROUTING --jump MASQUERADE
for each in /proc/sys/net/ipv4/conf/*
do
echo 0 > $each/accept_redirects
echo 0 > $each/send_redirects
done
/etc/init.d/ipsec restart
ipsec verify
cd /ztmp/l2tp
wget http://mirror.vpseek.com/sources/rp-l2tp-0.4.tar.gz
tar zxvf rp-l2tp-0.4.tar.gz
cd rp-l2tp-0.4
./configure
make
cp handlers/l2tp-control /usr/local/sbin/
mkdir /var/run/xl2tpd/
ln -s /usr/local/sbin/l2tp-control /var/run/xl2tpd/l2tp-control
cd /ztmp/l2tp
wget http://mirror.vpseek.com/sources/xl2tpd-1.2.4.tar.gz
tar zxvf xl2tpd-1.2.4.tar.gz
cd xl2tpd-1.2.4
make install
mkdir /etc/xl2tpd
rm -rf /etc/xl2tpd/xl2tpd.conf
touch /etc/xl2tpd/xl2tpd.conf
cat >>/etc/xl2tpd/xl2tpd.conf<<EOF
[global]
ipsec saref = yes
[lns default]
ip range = $iprange.2-$iprange.254
local ip = $iprange.1
refuse chap = yes
refuse pap = yes
require authentication = yes
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
EOF
rm -rf /etc/ppp/options.xl2tpd
touch /etc/ppp/options.xl2tpd
cat >>/etc/ppp/options.xl2tpd<<EOF
require-mschap-v2
ms-dns 8.8.8.8
ms-dns 8.8.4.4
asyncmap 0
auth
crtscts
lock
hide-password
modem
debug
name l2tpd
proxyarp
lcp-echo-interval 30
lcp-echo-failure 4
EOF
cat >>/etc/ppp/chap-secrets<<EOF
test l2tpd test123 *
EOF
touch /usr/bin/zl2tpset
echo "#/bin/bash" >>/usr/bin/zl2tpset
echo "for each in /proc/sys/net/ipv4/conf/*" >>/usr/bin/zl2tpset
echo "do" >>/usr/bin/zl2tpset
echo "echo 0 > \$each/accept_redirects" >>/usr/bin/zl2tpset
echo "echo 0 > \$each/send_redirects" >>/usr/bin/zl2tpset
echo "done" >>/usr/bin/zl2tpset
chmod +x /usr/bin/zl2tpset
iptables --table nat --append POSTROUTING --jump MASQUERADE
zl2tpset
xl2tpd
cat >>/etc/rc.local<<EOF
iptables --table nat --append POSTROUTING --jump MASQUERADE
/etc/init.d/ipsec restart
/usr/bin/zl2tpset
/usr/local/sbin/xl2tpd
EOF
clear
ipsec verify
printf "
####################################################
# #
# This is a Shell-Based tool of l2tp installation #
# Version: 1.2 #
# Author: Zed Lau #
# Website: http://zeddicus.com #
# #
####################################################
if there are no [FAILED] above, then you can
connect to your L2TP VPN Server with the default
user/pass below:
ServerIP:$vpsip
username:test
password:test123
PSK:$mypsk
"
Ubuntu 安裝腳本
#!/bin/bash
if [ $(id -u) != "0" ]; then
printf "Error: You must be root to run this tool!\n"
exit 1
fi
clear
printf "
####################################################
# #
# This is a Shell-Based tool of l2tp installation #
# Version: 1.2 #
# Author: Zed Lau #
# Website: http://zeddicus.com #
# For Ubuntu 32bit and 64bit #
# #
####################################################
"
vpsip=`ifconfig | grep 'inet addr:'| grep -v '127.0.0.1' | cut -d: -f2 | awk 'NR==1 { print $1}'`
iprange="10.0.99"
echo "Please input IP-Range:"
read -p "(Default Range: 10.0.99):" iprange
if [ "$iprange" = "" ]; then
iprange="10.0.99"
fi
mypsk="vpsyou.com"
echo "Please input PSK:"
read -p "(Default PSK: vpsyou.com):" mypsk
if [ "$mypsk" = "" ]; then
mypsk="vpsyou.com"
fi
clear
get_char()
{
SAVEDSTTY=`stty -g`
stty -echo
stty cbreak
dd if=/dev/tty bs=1 count=1 2> /dev/null
stty -raw
stty echo
stty $SAVEDSTTY
}
echo ""
echo "ServerIP:"
echo "$vpsip"
echo ""
echo "Server Local IP:"
echo "$iprange.1"
echo ""
echo "Client Remote IP Range:"
echo "$iprange.2-$iprange.254"
echo ""
echo "PSK:"
echo "$mypsk"
echo ""
echo "Press any key to start..."
char=`get_char`
clear
apt-get -y update
apt-get -y upgrade
apt-get -y install libgmp3-dev bison flex libpcap-dev ppp iptables make gcc lsof vim
mkdir /ztmp
mkdir /ztmp/l2tp
cd /ztmp/l2tp
wget http://www.openswan.org/download/openswan-2.6.24.tar.gz
tar zxvf openswan-2.6.24.tar.gz
cd openswan-2.6.24
make programs install
rm -rf /etc/ipsec.conf
touch /etc/ipsec.conf
cat >>/etc/ipsec.conf<<EOF
config setup
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
protostack=netkey
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=$vpsip
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
EOF
cat >>/etc/ipsec.secrets<<EOF
$vpsip %any: PSK "$mypsk"
EOF
sed -i 's/#net.ipv4.ip_forward=1/net.ipv4.ip_forward=1/g' /etc/sysctl.conf
sed -i 's/#net.ipv6.conf.all.forwarding=1/net.ipv6.conf.all.forwarding=1/g' /etc/sysctl.conf
sysctl -p
iptables --table nat --append POSTROUTING --jump MASQUERADE
for each in /proc/sys/net/ipv4/conf/*
do
echo 0 > $each/accept_redirects
echo 0 > $each/send_redirects
done
/etc/init.d/ipsec restart
ipsec verify
cd /ztmp/l2tp
wget http://mirror.vpseek.com/sources/rp-l2tp-0.4.tar.gz
tar zxvf rp-l2tp-0.4.tar.gz
cd rp-l2tp-0.4
./configure
make
cp handlers/l2tp-control /usr/local/sbin/
mkdir /var/run/xl2tpd/
ln -s /usr/local/sbin/l2tp-control /var/run/xl2tpd/l2tp-control
cd /ztmp/l2tp
wget http://mirror.vpseek.com/sources/xl2tpd-1.2.4.tar.gz
tar zxvf xl2tpd-1.2.4.tar.gz
cd xl2tpd-1.2.4
make install
mkdir /etc/xl2tpd
rm -rf /etc/xl2tpd/xl2tpd.conf
touch /etc/xl2tpd/xl2tpd.conf
cat >>/etc/xl2tpd/xl2tpd.conf<<EOF
[global]
ipsec saref = yes
[lns default]
ip range = $iprange.2-$iprange.254
local ip = $iprange.1
refuse chap = yes
refuse pap = yes
require authentication = yes
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
EOF
rm -rf /etc/ppp/options.xl2tpd
touch /etc/ppp/options.xl2tpd
cat >>/etc/ppp/options.xl2tpd<<EOF
require-mschap-v2
ms-dns 8.8.8.8
ms-dns 8.8.4.4
asyncmap 0
auth
crtscts
lock
hide-password
modem
debug
name l2tpd
proxyarp
lcp-echo-interval 30
lcp-echo-failure 4
EOF
cat >>/etc/ppp/chap-secrets<<EOF
test l2tpd test123 *
EOF
touch /usr/bin/zl2tpset
echo "#/bin/bash" >>/usr/bin/zl2tpset
echo "for each in /proc/sys/net/ipv4/conf/*" >>/usr/bin/zl2tpset
echo "do" >>/usr/bin/zl2tpset
echo "echo 0 > \$each/accept_redirects" >>/usr/bin/zl2tpset
echo "echo 0 > \$each/send_redirects" >>/usr/bin/zl2tpset
echo "done" >>/usr/bin/zl2tpset
chmod +x /usr/bin/zl2tpset
iptables --table nat --append POSTROUTING --jump MASQUERADE
zl2tpset
xl2tpd
cat >>/etc/rc.local<<EOF
iptables --table nat --append POSTROUTING --jump MASQUERADE
/etc/init.d/ipsec restart
/usr/bin/zl2tpset
/usr/local/sbin/xl2tpd
EOF
clear
ipsec verify
printf "
####################################################
# #
# This is a Shell-Based tool of l2tp installation #
# Version: 1.2 #
# Author: Zed Lau #
# Website: http://zeddicus.com #
# For Ubuntu 32bit and 64bit #
# #
####################################################
if there are no [FAILED] above, then you can
connect to your L2TP VPN Server with the default
user/pass below:
ServerIP:$vpsip
username:test
password:test123
PSK:$mypsk
"
連線異常排除
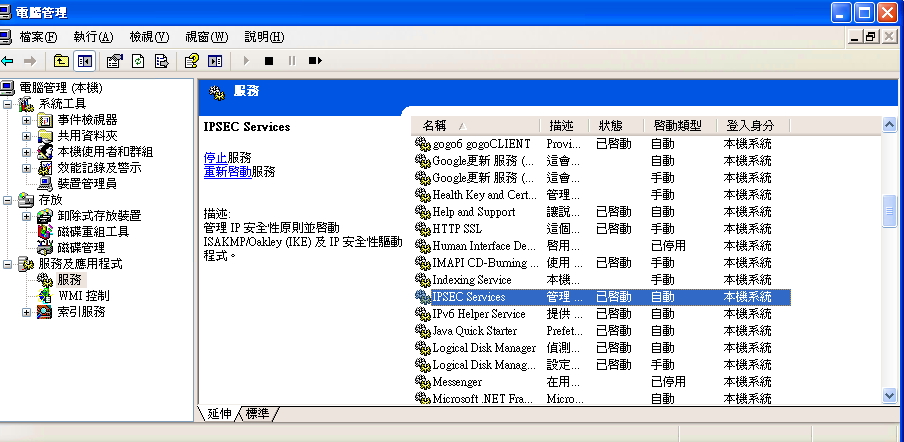
1.XP 用戶:請確保“控制台->管理工具->服務”中的 IPSEC 服務被啟動
2.win7、win2008 server出現提示766、781、789、792等缺少證書類錯誤
新建ipsec.txt後更改尾碼名為reg並執行它
重啟你的電腦
電腦啟動後,重新連接
ipsec.reg檔內容如下:
REGEDIT4 [HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters] "prohibitipsec"=dword:00000001
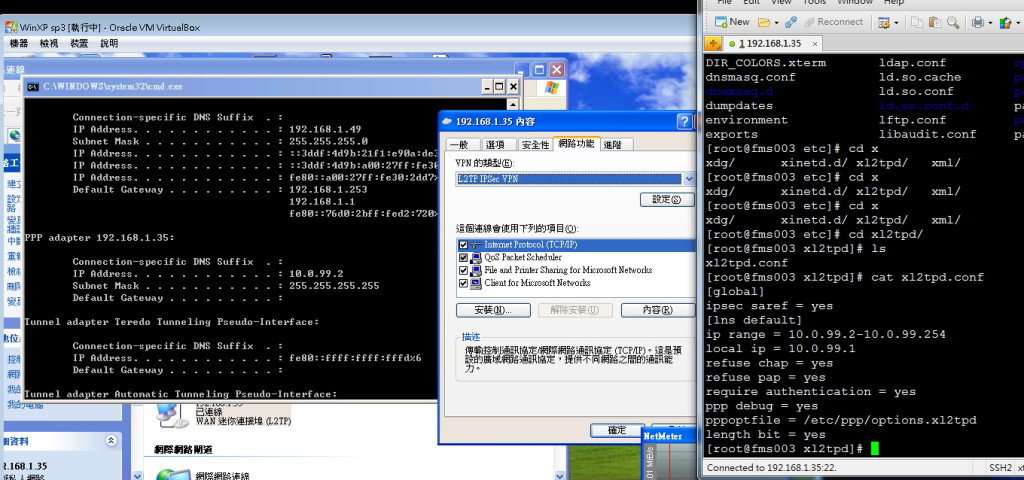
連線L2TP設定如下圖
l2tp設定部份
/etc/xl2tpd/xl2tpd.conf
修改/etc/xl2tpd/xl2tpd.conf ip range = 您希望對方可以得到哪些ip local ip = server 對內ip ex: [lns default] ip range = 192.168.0.11-192.168.0.13 local ip = 192.168.0.1 require chap = yes refuse pap = yes require authentication = yes name = LinuxVPNserver ppp debug = yes pppoptfile = /etc/ppp/options.xl2tpd length bit = yes
修改 /etc/ppp/options.xl2tpd ms-dns = 內部ms dns的ip ex: ipcp-accept-local ipcp-accept-remote ms-dns 192.168.0.2 noccp auth crtscts idle 1800 mtu 1410 mru 1410 defaultroute debug lock proxyarp connect-delay 5000
ipsec 設定(預先共用金鑰)
6.1 設定 psk (pre-shared-key)
vi /etc/ipsec.d/william.secrets
###############################
%any: PSK "your shared key"
server_ip: PSK "your shared key"
###############################
其中 server_ip 是您的server 對外ip,
"your shared key"是你的共用金鑰
6.2 vi /etc/ipsec.conf
#############################################
version 2.0 # conforms to second version of ipsec.conf specification
# basic configuration
config setup
# Debug-logging controls: "none" for (almost) none, "all" for lots.
# klipsdebug=none
# plutodebug="control parsing"
# For Red Hat Enterprise Linux and Fedora, leave protostack=netkey
protostack=netkey
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
# Enable this if you see "failed to find any available worker"
nhelpers=0
#You may put your configuration (.conf) file in the "/etc/ipsec.d/" and uncomment this.
#include /etc/ipsec.d/*.conf
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=<你的對外ip>
leftprotoport=17/1701
right=%any
rightprotoport=17/%any